Understanding PCI DSS: How to Safeguard Cardholder Data
Written on
Chapter 1: Introduction to PCI DSS
In March 2024, the updated version of the Payment Card Industry Data Security Standard (PCI DSS) is set to take effect. My previous article discussed the significant changes on the horizon and offered guidance for organizations to prepare for these updates. However, the essence of PCI DSS remains anchored in Requirement 3: Protect Cardholder Data. This requirement outlines how businesses should safeguard cardholder information, regardless of whether it is stored, processed, or transmitted.
In my experience conducting numerous PCI DSS audits, I've observed that many organizations struggle with managing cardholder data correctly. The PCI DSS is explicit about what information can and cannot be stored. Non-compliance with Requirement 3 can lead to failed audits, making it crucial to understand.
Requirement 3 encompasses the protection of cardholder data, whether it appears on screens, printed materials, or in digital storage. Below are some of the techniques outlined in PCI DSS for achieving this protection:
Video Description: This video provides a free preview of a PCI DSS course, focusing on how to protect cardholder data effectively.
Section 1.1: Techniques for Protecting Cardholder Data
The following methods are commonly employed to safeguard cardholder information:
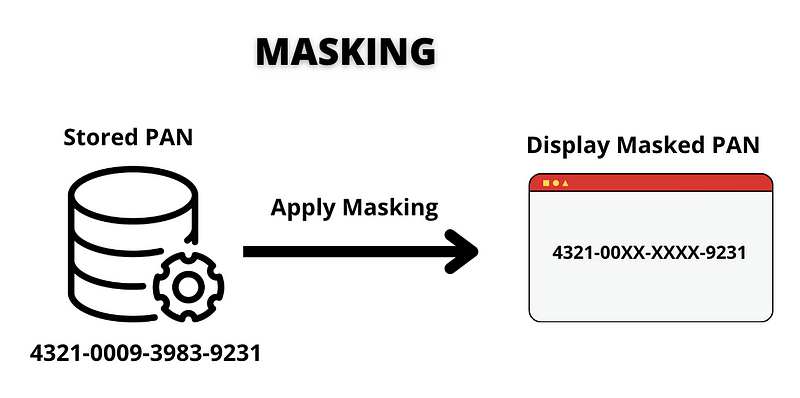
Masking
Masking is a technique that conceals part of a primary account number (PAN) when displayed or printed, such as on receipts or screens, especially when there is no business necessity to display the entire number. Typically, the first six and last four digits can be shown, even if the full PAN is stored.
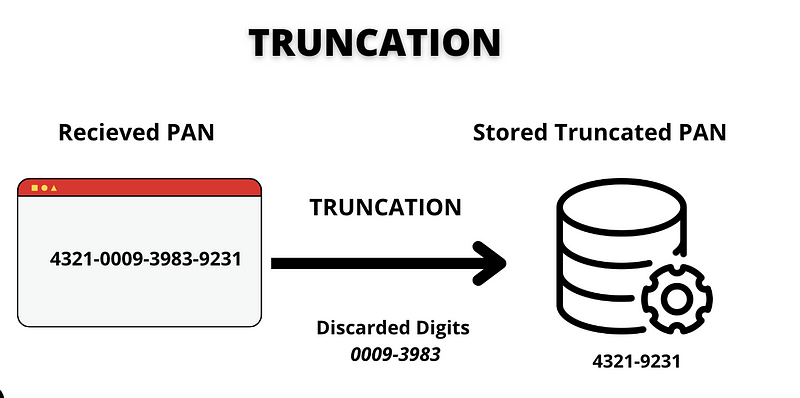
Truncation
Truncation involves removing segments of the PAN to render it unreadable, making it effectively unusable for any future transactions. This method is often applied to stored PANs.
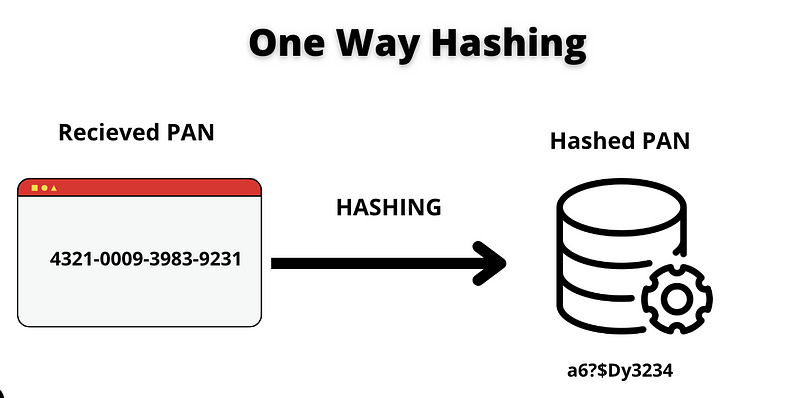
One-Way Hashing
Hashing is a process that transforms a PAN into a unique string or "hash" that cannot be reversed to reveal the original number. This method is beneficial for detecting changes and is effective for safeguarding stored PANs.
Note: Storing both truncated and hashed versions of the same PAN is prohibited unless additional controls are implemented, as this could facilitate the reconstruction of the PAN by attackers.
Section 1.2: Advanced Techniques
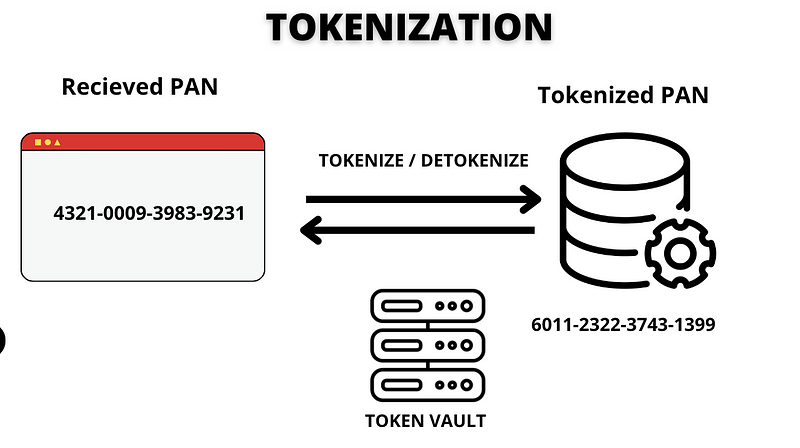
Tokenization
Tokenization replaces the original PAN with a "token," typically a random 16-digit number. This approach maintains the original format, easing integration with existing systems while minimizing risk and PCI compliance scope. Tokens can be reverted back to the original PAN but lack intrinsic value for attackers.
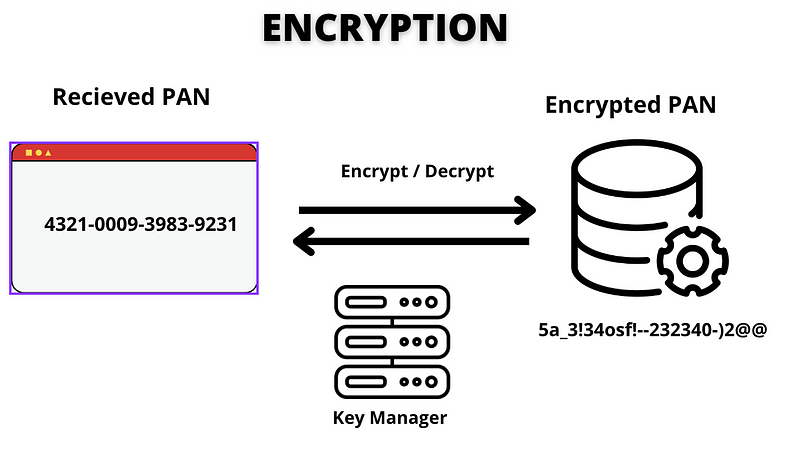
Encryption
Encryption involves using a cryptographic key to secure the PAN, differing from tokenization in that it may alter the original 16-digit format. Encryption relies on mathematical relationships between the encrypted data and the original PAN, which poses different challenges compared to tokenization.
Choosing the Right Technique
All of these techniques are effective, and the choice should be based on your organization’s operational needs and technological capabilities. Each method has its advantages and disadvantages, allowing for flexible implementation according to PCI DSS guidelines. It’s advisable to consult with your auditors early on to determine what strategies will best suit your environment.
Thanks for reading! If you are keen on diving deeper into PCI DSS, consider joining my discounted PCI DSS Masterclass, where I cover the standard in detail and prepare you for the upcoming changes!
